Dropm0rt V0.1 beta
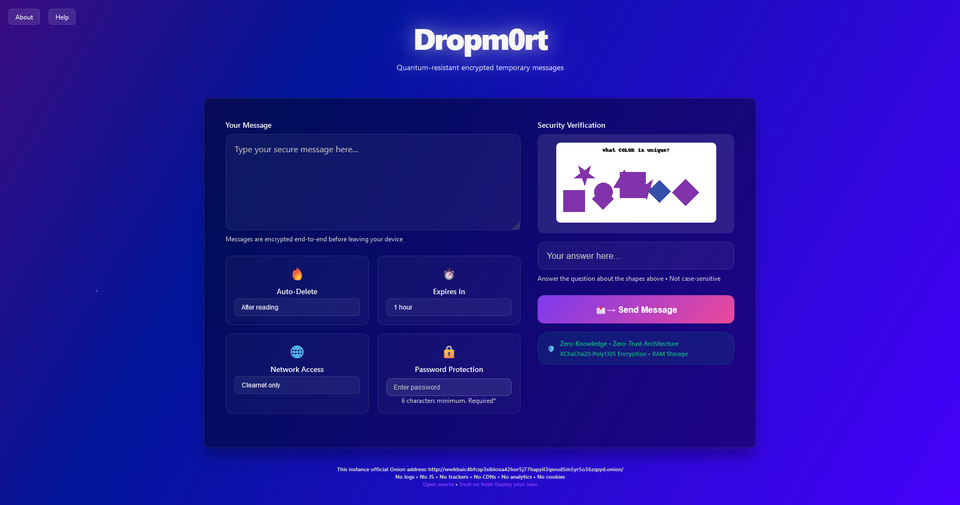
Dropm0rt is a quantum-resistant, self-destructing message system that provides true end-to-end encryption for sensitive communications.
Even though it was designed to be self-hosted you can already use our instance at: https://dropm0rt.org
Source code*:
https://gitlab.com/NoBravado/dropm0rt
*(I still have some cleanup to do on the code before publishing _ Sept 16 2025)
The whole point of free & open-source software is for everyone qualified to be able to participate & enhance the app security & functionalities , so get involved ;)
Insights:
- Dual-Layer Encryption: Messages are encrypted twice - first with your password using Argon2id key derivation, then with a server-generated key using AES-256-GCM or XChaCha20-Poly1305 for quantum resistance.
- Perfect Forward Secrecy: Ephemeral X25519 key exchange with automatic key rotation ensures past communications remain secure even if future keys are compromised.
- CAPTCHA-Protected Access: Anti-OCR CAPTCHAs with cryptographic commitments prevent automated attacks and ensure verification.
- Self-Destructing Storage: Messages are automatically purged from Redis after reading or TTL expiration (1 hour to 7 days). Burn-after-read option available.
- Memory Protection: Cryptographic keys are securely zeroed from memory after use to prevent recovery.
- Traffic Analysis Protection: Random timing delays and decoy traffic generation prevent correlation attacks and traffic pattern analysis.
- Zero-Logging Mode: Optional complete logging suppression for maximum operational security in high-risk environments.
- Canary Token System: Honeypot tokens detect unauthorized access attempts and trigger immediate breach alerts.
- Emergency Shutdown: Dead man's switch and secure emergency procedures for crisis situations with automatic data destruction.
- Rate Limited: Strict rate limiting prevents abuse - 10 messages per hour, 5 CAPTCHAs per minute.
- Minimal Metadata: Only essential cryptographic parameters are stored - no timestamps, IP addresses, or user tracking.
- Constant-Time Operations: CAPTCHA validation uses HMAC-based constant-time comparison to prevent timing attacks.
- Dual Network Access: Available via clearnet HTTPS and Tor onion service for maximum privacy and censorship resistance.
- Thread-Safe Sessions: Session management uses locks to prevent race conditions during concurrent access.
How It Works:
Your message undergoes a multi-stage encryption process:
- Client-Side: Message is padded and compressed using zlib
- Password Layer: Encrypted with Argon2id-derived key (100,000+ iterations, 32-byte salt)
- Perfect Forward Secrecy: Ephemeral X25519 ECDH key exchange generates session-specific encryption keys
- Server Layer: Re-encrypted with quantum-resistant algorithms and ephemeral keys
- Storage: Stored in Redis with minimal metadata and automatic expiration
Retrieval Process: Messages are decrypted in reverse order with constant-time validation to prevent side-channel attacks. Canary tokens are checked before decryption to detect breach attempts.
Security Monitoring: Real-time breach detection, traffic analysis protection, and emergency communication channels ensure operational security for high-risk users.